

Fentress Incorporated partners with Major Security Consulting & Design, LLC, to perform security assessments of school systems and educational facilities, public safety facilities, and public and private office buildings to identify security vulnerabilities and provide recommendations for improvement. The Major-Fentress Team has worked seamlessly together on multiple security assessment projects. When combined, we have conducted over 1,700 facility and security assessments nationwide.
Our security assessments have included the following:
Read on for a description of our tested process, including our proprietary SAFE tool, to determine if an assessment could benefit your organization.

Providing a safe and secure facility that can respond to various threats is a primary concern for designers and building owners. While this is fairly straightforward when planning a new facility, many existing facilities were not designed to meet modern security and safety standards. In these instances, an objective security assessment process can help identify critical deficiencies and prioritize solutions to address those deficiencies.
The security assessment should be an independent and systematic evaluation of a facility’s threats, risks, and vulnerabilities. A comprehensive evaluation includes analysis to determine a facility’s physical security and its safety protocols’ effectiveness. By objectively identifying a facility’s physical and operational strengths and weaknesses, recommendations for short-, mid-, and long-term security improvements can be made. Ultimately, a successful security assessment provides owners with a product that will help them prioritize improvements and support budgetary decisions.

Our goal is to clearly understand the security strengths and challenges within existing facilities and operations, identify improvement opportunities, and support budgetary decisions through prioritized recommendations.

Safety and security in our nation’s schools is a paramount concern. Our goal is to help schools understand the vulnerabilities and threats they face and provide them with actionable solutions to improve security. We are experienced in conducting assessments for elementary, middle, and high schools, as well as colleges and universities. Please watch the video below for information on our proven school security assessment process.
A primary mission of public safety personnel, including law enforcement and fire and rescue personnel is to protect the safety and wellbeing of others. Less thought may be given to protecting the safety and security of public safety personnel in the buildings where they work. Public safety facilities are increasingly becoming targets of large-scale demonstrations, threats, and acts of violence that put the safety of their occupants at risk.
Our team of CPTED-certified personnel helps protect the security of public safety and law enforcement facilities, including police stations, fire stations, public safety departments, emergency medical services departments, and search and rescue departments. We do this by conducting comprehensive and objective assessments to identify security vulnerabilities and providing actionable data and recommendations to help guide security decisions. We strive to protect those who protect and serve.
With political discord and anti-government sentiment running high across our nation, it is of vital importance to ensure the security of government buildings and the safety of their occupants. We help protect the security of government facilities by conducting comprehensive and objective assessments across a wide range of federal, state, and local government facilities.
We have completed security assessments in over 1,700 government buildings, including those listed below.
Our assessment team is comprised of CPTED-certified personnel with decades of police experience, a criminal justice educator at the university level, licensed architects, and planners with extensive experience conducting security assessments. Our approach is based on best practices in security and proven security standards. Our process produces actionable data and recommendations to help guide security decisions.


The figure below displays our security assessment process and results.
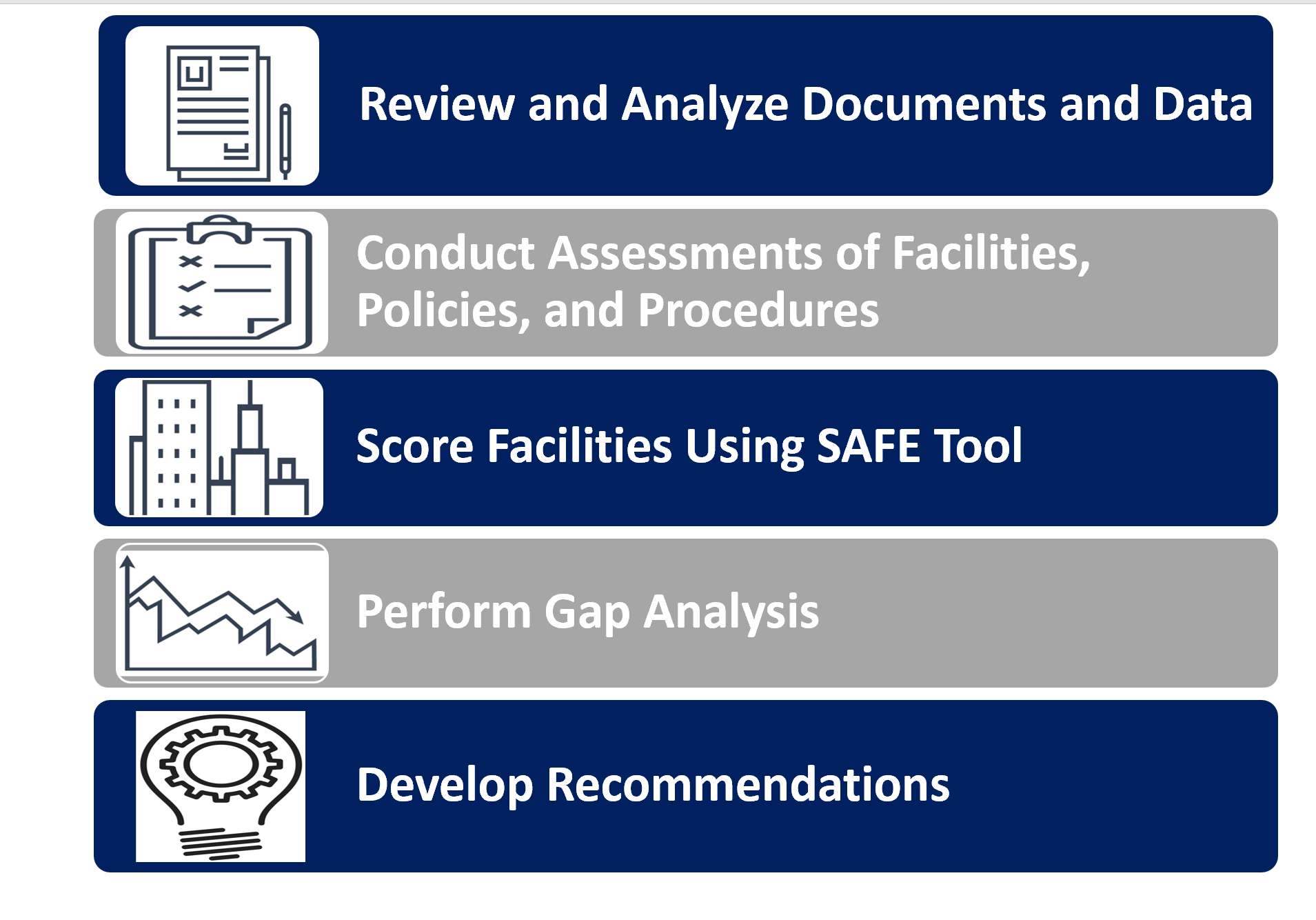
Our comprehensive process is a unique combination of quantitative and qualitative analysis.
Our innovative Security Assessment and Facility Evaluation (SAFE) tool drives the quantitative analysis. We have developed a rigorous and comprehensive process that utilizes the SAFE tool to evaluate and score how well an organization’s physical space and operations meet its security and safety requirements. The SAFE tool contains a wide array of security performance metrics and can be tailored for the unique security requirements of each organization, including:
We recognize that a security assessment should focus on more than just the building layout, security systems, and policies. Security involves people - at all levels. The qualitative elements of our process include facilitated group sessions and interviews with key personnel at each location. This allows us to gather input on the culture of the building’s occupants and existing security policies and procedures and their effectiveness. The involvement of key stakeholders during these assessments is critical, as individual facilities often vary in how they interpret, implement, and follow security procedures. Therefore, during each site visit, facilitated interviews are held with key staff, including primary tenant representatives, security personnel, facility managers, and other designated personnel, to discuss the unique culture of each facility, system deficiencies, and the operational procedures and practices in place for security. These interviews also allow personnel to provide feedback about security programs and practices that have worked well and areas of need.

 Williamsburg-James City County Public Schools is happy to recommend Major-Fentress. They have recently (April 2022) completed a Threat, Risk, and Vulnerability Assessment for our 16 schools and three administration buildings. Major-Fentress communicated with us throughout the process from beginning to end. They delivered a product that was very useful to us in our ongoing mission to improve our building safety and security. They identified 70 overall recommendations and improvements ranking them, categorizing them and even including cost estimates to improve those areas. Their use of the SAFE tool and subsequent scores made it very easy to identify schools that needed improvement and those that were already in a pretty good position as far as safety and security is concerned.
Williamsburg-James City County Public Schools is happy to recommend Major-Fentress. They have recently (April 2022) completed a Threat, Risk, and Vulnerability Assessment for our 16 schools and three administration buildings. Major-Fentress communicated with us throughout the process from beginning to end. They delivered a product that was very useful to us in our ongoing mission to improve our building safety and security. They identified 70 overall recommendations and improvements ranking them, categorizing them and even including cost estimates to improve those areas. Their use of the SAFE tool and subsequent scores made it very easy to identify schools that needed improvement and those that were already in a pretty good position as far as safety and security is concerned.
The entire process working with Major-Fentress was smooth and seamless, from the bid award to the school board presentation, we could not have asked for a better partner to work with. Mike Jones was in constant communication with myself and others involved in the project, not just about our TRV assessment but with world and local events that may have affected school security. Keith Fentress was very helpful with questions regarding the SAFE tool and scores as questions arose from other key stakeholders in our division along the way.
Again, I am happy to recommend Major-Fentress.
Brian Weaver
Supervisor for Building Security and Services
Williamsburg-James City County Public Schools
Overview
The SAFE tool is used by our team of architects and security assessors during the assessment of an existing facility to identify critical deficiencies and calculate a SAFE score for each location. It includes over 200 security-related factors and accompanying performance measures, which can be tailored to assess a specific type of building (or portfolio of buildings) in any location.
Once tailored to meet an organization’s security assessment goals, this interactive tool provides a consistent and objective set of factors that will be evaluated within each facility. This allows our team to gather the data in a standardized manner efficiently. During a facility assessment, our architects utilize a secure tablet computer to rate individual performance measures, take notes, and document observations. This functionality allows us to record all ratings as the assessment is conducted in real-time.
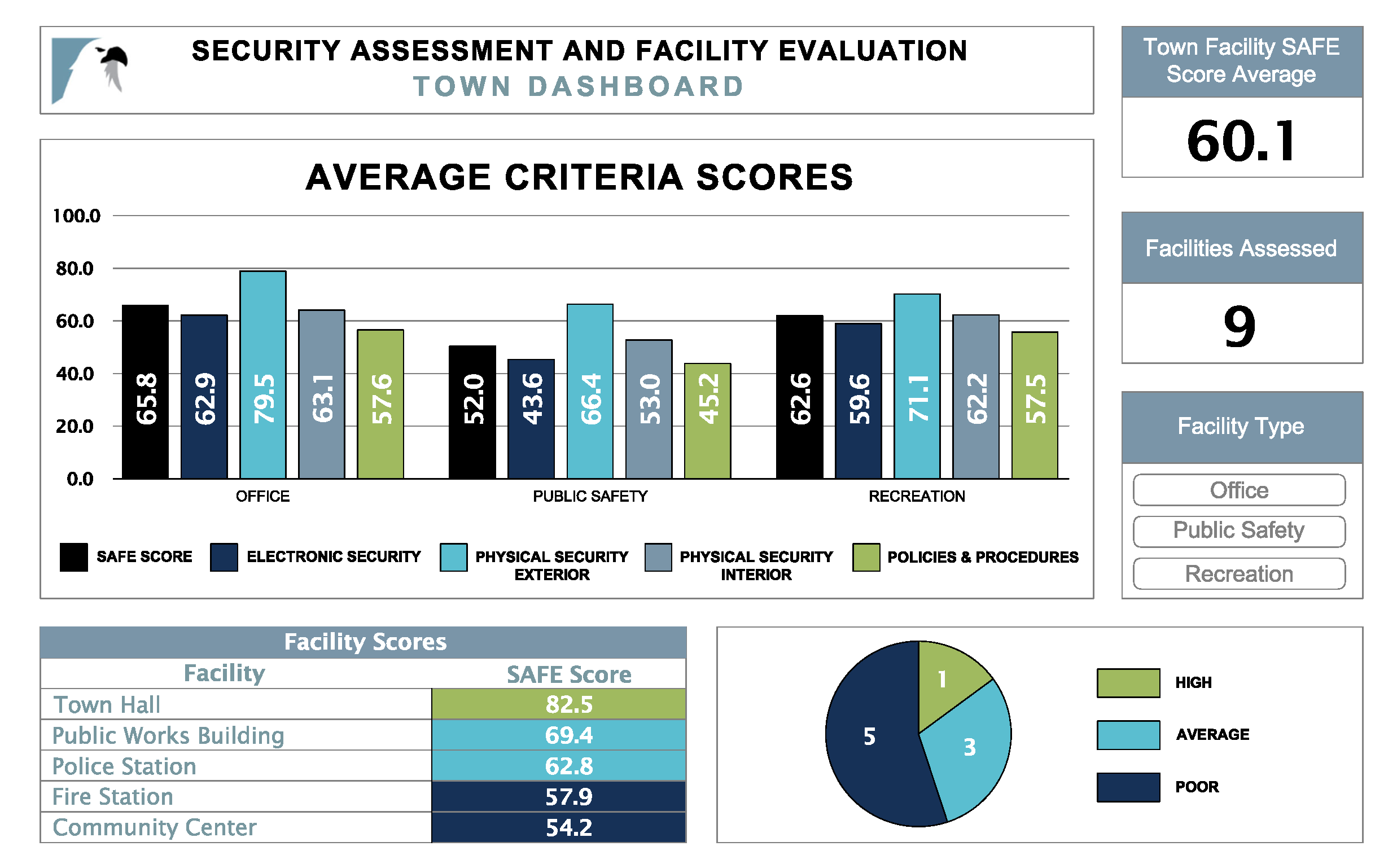
The SAFE tool produces an immediate comparable overall score for each facility. It establishes a database that is sortable in various ways to allow an owner to quickly identify critical security needs in one facility or across an entire portfolio. This information can then support prioritizing recommended security improvements at each location.
Categories and Results
The security factors included in the SAFE score fall into four major categories:
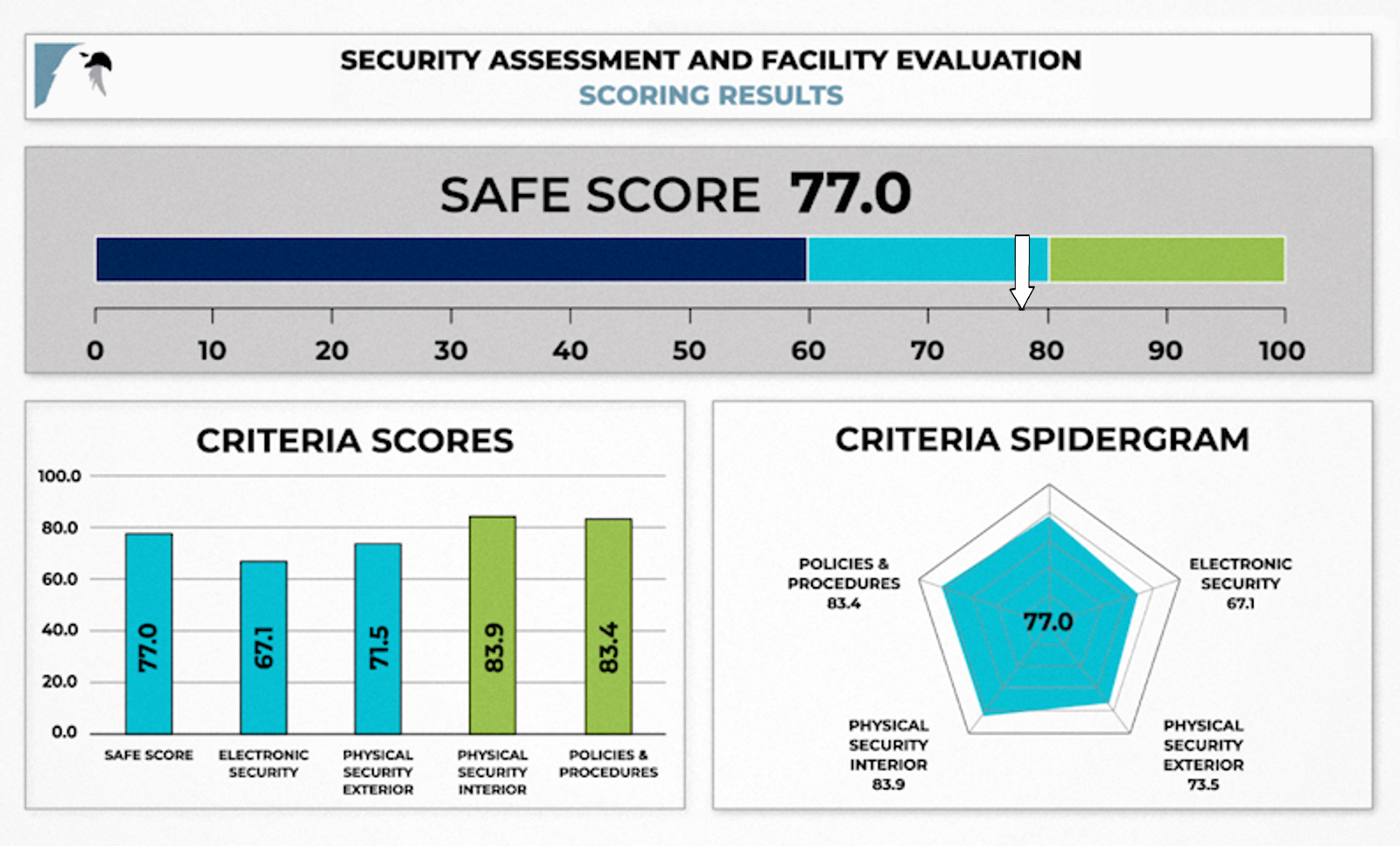
The SAFE tool automatically produces an overall assessment score (the SAFE score) on a scale of 0 to 100, with a score of 100 representing ideal facility security within the context of the evaluation criteria. To calculate the score, the SAFE tool incorporates the Analytic Hierarchy Process (AHP), a well-defined mathematical structure for organizing and analyzing complex decisions.
The figure below depicts a sample output of the SAFE tool results dashboard. In addition to the overall SAFE score, the results summary includes individual SAFE scores for each of the four key areas noted above. In general, a grade of 90-100 represents a facility that offers optimal security, a grade of 80-89 represents a facility that meets most security standards, a grade of 60-79 represents a facility that is lacking in significant areas of security, and a grade of 60 or lower represents a facility that is in serious need of critical security updates.

CPTED is a holistic and multidisciplinary approach to security and crime prevention that uses architectural design and behavioral science to make a space, site, or area more safe and secure. CPTED places emphasis on designing, planning, and manipulating the built environment to increase the perceived risk of detection and apprehension. The SAFE tool incorporates factors that are based on the following CPTED principles.
Together these CPTED principles create what is known as a “defensible space.” The CPTED principles are incorporated into developing strategies that mitigate safety and security deficiencies identified by the assessment.

Our security assessment process provides organizations with the following comprehensive set of decision-making tools:
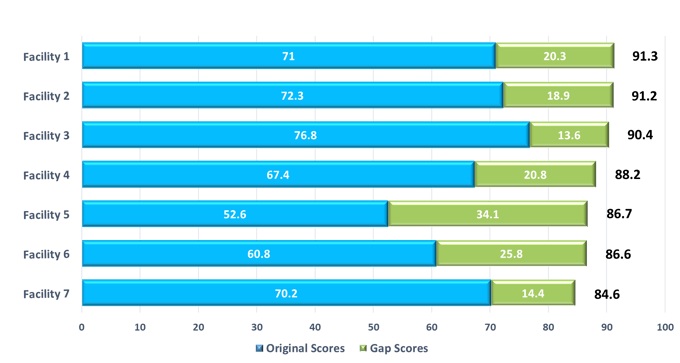
This analysis, called a “gap analysis,” is illustrated in the figure below, which shows how an improvement strategy can “fill the gap” and increase a facility security score.

Our security assessments provide the information leadership needs to develop a defensible strategy to improve security across their portfolio, including the following:
.jpg)
.jpg)